Identity Patterns with the WSO2 Identity Server
Enforce users to provide missing required attributes while getting JIT provisioned to the local system
Problem:
Enforce users to provide missing required attributes while getting JIT provisioned to the local system
Problem:
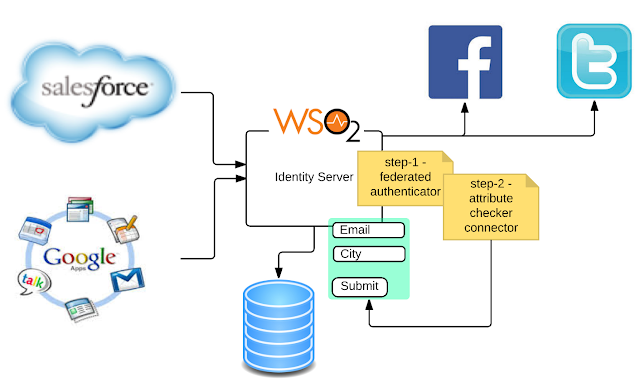
- The business users need to access multiple service providers via federated identity provider (i.e Facebook, Yahoo, Google).
- Need to JIT provision all the user coming from federated identity providers with a predefined set of attributes.
- If any required attributes are missing in the authentication response from the federated identity provider, the system should present a UI to the user to provide those.
- Deploy WSO2 Identity Server as the Identity Provider and register all the service providers and federated identity providers.
- Enable JIT provisioning for each federated identity provider.
- Build a connector to validate the attributes in the authentication response and compare those against the required set of attributes. The required set of attributes can be defined via a claim dialect. If there is a mismatch between the attributes from the authentication response and the required set of attributes then this connector will redirect the user to web page (deployed under authenticationendpoints web app) to accept the missing attributes from the user.
- Engage the attribute checker connector from the previous step to an authentication step after the step, which includes the federated authenticator.
- Products: WSO2 Identity Server 5.0.0+