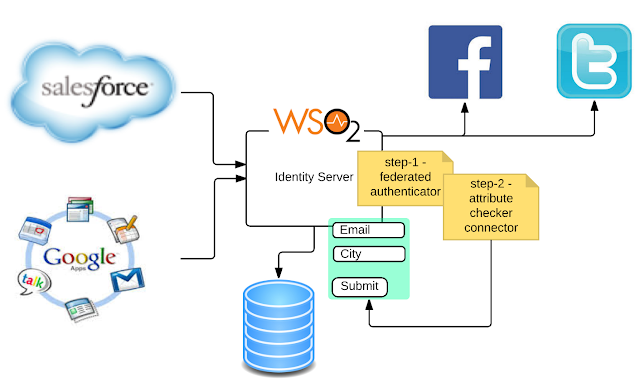
Identity Patterns with the WSO2 Identity Server
User administrators by the user store
Problem:
- Define user administrators by user store. For example, a user belongs to the role foo-admin will be able to perform user admin operations on the foo user store, while he/she won’t be able to perform user admin operations on the bar user store.
- Deploy the WSO2 Identity Server as an identity provider over multiple user stores.
- Define a XACML policy, which specified who should be able to do which operation on user stores.
- Create a user store operation listener and talk to the XACML PDP during user admin operations.
- Create roles by user store and user administrators to appropriate roles. Also, make sure each user administrator has the user admin permissions from the permission tree.
- Products: WSO2 Identity Server 4.6.0+